Google Cloud - Security Alerts Automation
.png)
In this blog, we will guide you through automating alerting for critical activities and securing your projects against accidental deletion using custom scripts. Setting up log-based metrics and alerts manually can be a time-consuming task, typically taking around an hour or might be manual errors. To optimize this process and enhance efficiency, we have automated it using a combination of Shell and YAML scripts.
By implementing this solution, you can configure notification channels to receive alerts whenever changes are detected in your cloud environment, ensuring prompt action on potential issues. Our approach involves leveraging YAML files along with the Deployment Manager to create and manage Log Metrics and Alerting Policies. Once these components are successfully deployed, the deployment itself is deleted since it does not interfere with any ongoing services or resources in your cloud environment.
The following steps will provide you with a detailed, step-by-step guide to implementing this automation effectively, allowing you to maintain better security and operational efficiency.
Step-by-step guide to implementing this automation effectively
1. Clone the Repository
Prerequisites:
Connect to your Google Cloud Shell and ensure you have the necessary permissions to implement the script.
git clone https://github.com/nvrvenkat/Securitylogalerts.git
This command clones the Securitylogalerts repository from GitHub to your local system.
2. Navigate to the Repository Directory
cd Securitylogalerts/
This command changes the directory to the Securitylogalerts folder, where all project files are located.
3. Description of Metrics and Alerts
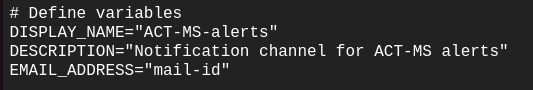
4. Replace the Email Address in logmetric_notification.sh
Update the email address in the shell script “logmetric_notification.sh” with the specific email address where alerts need to be sent.
This email address will be used to configure the notification channel.
5. Execute the Notification Channel Script
./logmetric_notification.sh
Runs the script to create a notification channel with the updated email address.
It will create a notification channel with the updated email address and generate log-based metrics as specified in the "Metrics and Alerts" section.
Note: If a notification channel already exists, execute the logmetric.sh file to generate only the log-based metrics.
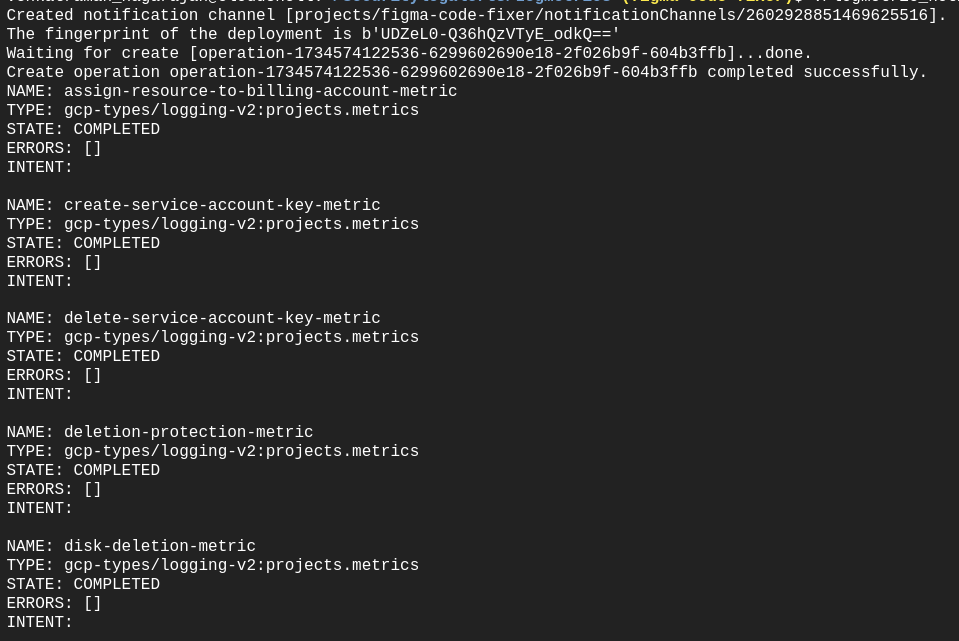
6. Navigate to the Log Alert Directory and Execute Scripts
a) cd /Securitylogalerts/Logalert
./scripts.sh
The scripts.sh script triggers:
replace_notification_channel.sh: Replaces the notification channel with ACT-MS-alerts in the YAML files used for creating log metric alerts. The output is saved to output.txt.
logalert.sh: Creates alerting policies based on the updated notification channel in the YAML files.
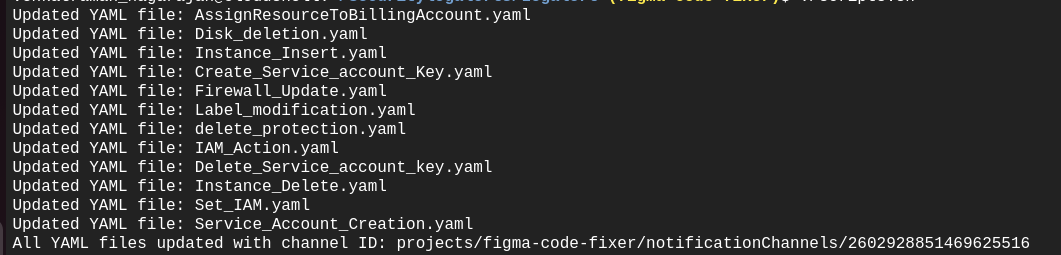
Alerting Policies Update:
- Once scripts.sh is executed, the notification channel in the YAML files will be replaced, and the alerting policies will be created.
- The alerting policies should be fully deployed within approximately 10 minutes.
The resources will be created using the Deployment Manager in the Google Cloud Console. Once the resources are created, the deployment will be deleted while retaining the resources.
b)Add Multiple Notification Channels (optional):cd /Securitylogalerts/Logalertmultiple./scripts.sh
This command adds multiple notification channels to the alerting policies. Ensure you update the respective notification channel names in the “replace_notification_channel.sh” file before executing the script.It updates the YAML files for log alert metrics with the additional notification channels.
7. Test Alerting Policies
This script tests the alerting policies by:
- Creating and deleting resources (e.g., instances, disks, service accounts, service account keys, and firewall rules).
- Sending alerts to the configured notification channel to verify that the policies are functioning correctly.
8. Resource Creation and Deletion Activity
After executing “alerttest.sh”, resources are automatically created and deleted as per the alerting policy configurations.
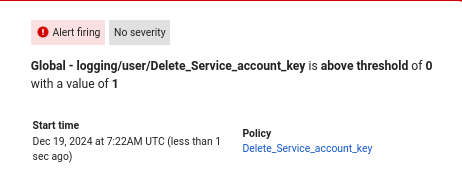
Alerts are triggered and sent to the configured notification channel.
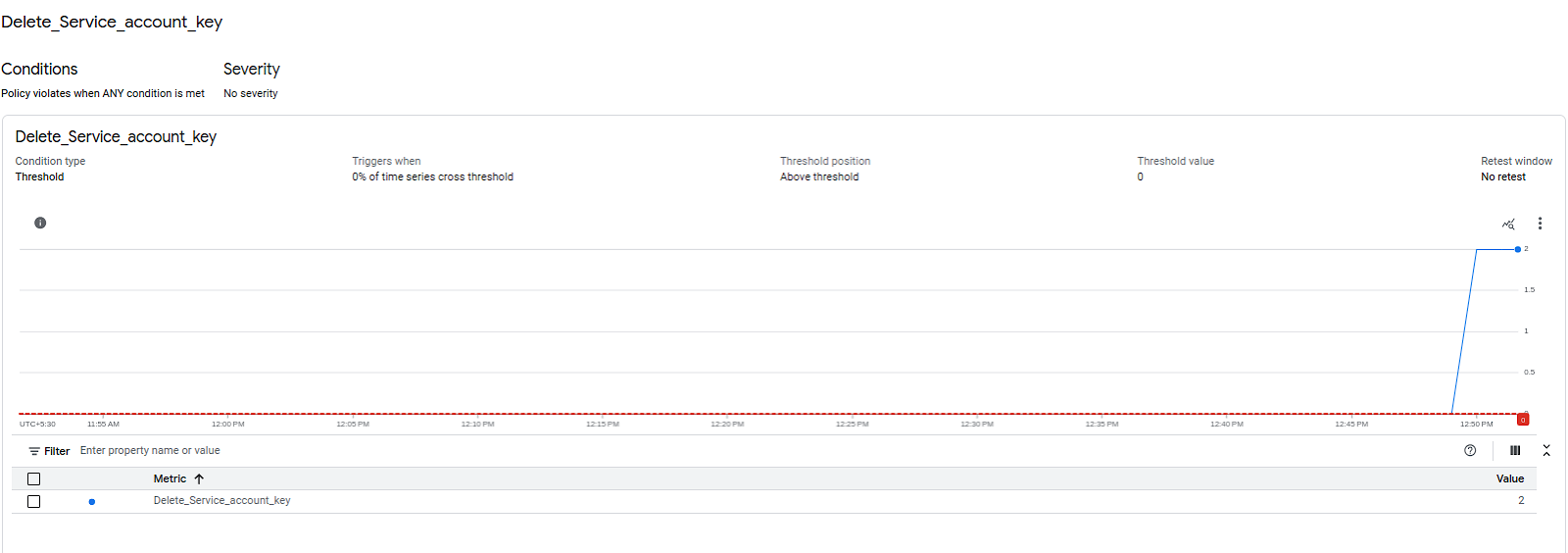
For example: Alerts for service account key creation and deletion.
Similar alerts for other resources will be triggered based on resource creation.
9.Enable Project Liens:
cd /Securitylogalerts/
./Liens.sh
Executes the “Liens.sh” script, which fetches the project ID automatically and enables liens on the project to prevent accidental deletion.
By following these steps, you'll be able to automate your cloud environment’s monitoring and security processes, ensuring that you stay ahead of any potential data and revenue losses and minimize the risk of accidental deletions.



